As a follow-up to our previous exploration of SMTP fundamentals, this article dives deep into SMTP tarpitting—what it is, how it works, and why it matters for your email infrastructure.
What is SMTP Tarpitting?
SMTP tarpitting is a defensive technique implemented on email servers that deliberately slows down the SMTP conversation between the sending and receiving mail servers. Named after “tar pits” (sticky prehistoric traps that captured animals), this technique essentially creates a “sticky” situation for potential abusers by introducing artificial delays in the SMTP transaction process.
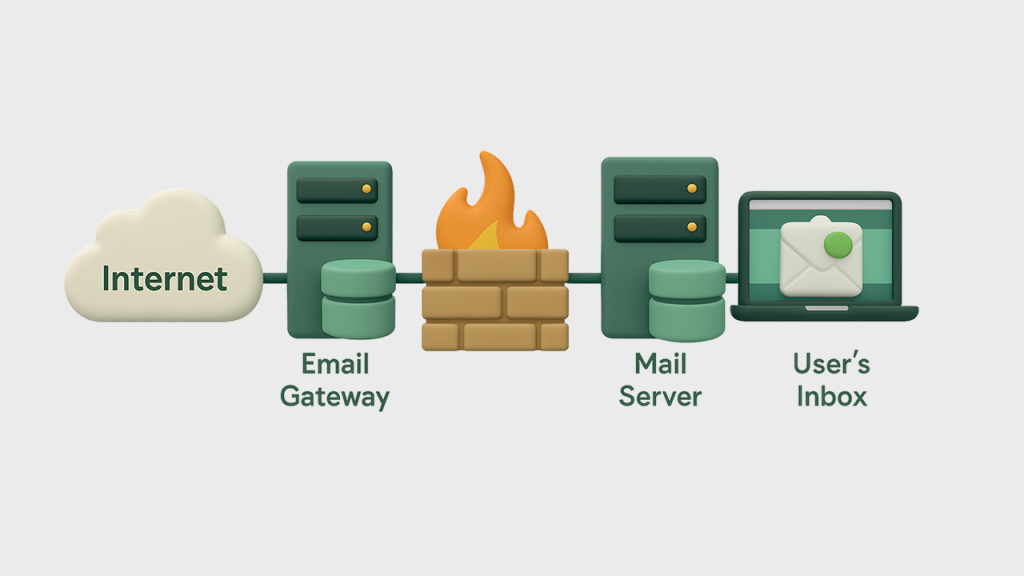
When a mail server employs tarpitting, it intentionally adds delays at various stages of the SMTP conversation, particularly when receiving messages from suspicious sources. Furthermore, these delays are strategically implemented to create minimal impact on legitimate communications. However, while these delays might be imperceptible for legitimate senders, they simultaneously become significantly problematic for spammers who rely on sending large volumes of messages quickly.
Moreover, the effectiveness of tarpitting lies in its ability to exploit the fundamental difference between legitimate and malicious email patterns. Consequently, legitimate users typically send relatively few messages and can tolerate brief delays without noticing any disruption. In contrast, spammers operate under entirely different constraints, as they depend on rapid message delivery to maintain their profit margins. Therefore, even small delays can dramatically reduce their operational efficiency.
Additionally, tarpitting serves as a passive defense mechanism that requires minimal server resources while effectively deterring abuse. As a result, this technique has become increasingly popular among email administrators seeking cost-effective anti-spam solutions. Nevertheless, the implementation must be carefully calibrated to ensure that legitimate users remain unaffected while still providing sufficient deterrent effect against unwanted bulk email campaigns.
How SMTP Tarpitting Works
To understand how tarpitting works, let’s first recall the basic SMTP conversation flow:
- Connection establishment – The sending server connects to the receiving server
- Greeting exchange – Servers identify themselves
- MAIL FROM command – Sender specifies the message source
- RCPT TO command – Sender identifies recipient(s)
- DATA command – Sender transmits the message content
- Termination – The connection closes
Tarpitting can introduce delays at any of these stages. Most commonly, delays are added:
- After receiving the MAIL FROM command
- Between consecutive RCPT TO commands
- After the DATA command
- When detecting suspicious patterns or known spam indicators
These delays typically range from a few seconds to several minutes, depending on the server’s configuration and the perceived threat level of the connecting client.
The Technical Implementation
At its core, SMTP tarpitting is implemented through timing controls in the mail server software. For example, in Postfix (a popular mail transfer agent), tarpitting can be configured using the smtpd_recipient_limit and smtpd_recipient_delay parameters.
In Microsoft Exchange, similar functionality is achieved through connection filtering and throttling policies.
Why Tarpitting Is Effective
SMTP tarpitting works because of fundamental differences between legitimate email operations and spam campaigns:
- Economics of scale: Spammers need to send millions of messages quickly to be profitable. Even small delays can dramatically reduce their throughput.
- Connection resources: Forcing spammers to maintain longer connections consumes their resources and limits their ability to establish new connections.
- Asymmetric impact: A 5-second delay is barely noticeable for legitimate email but devastating for operations sending to thousands of recipients.
- Behavior exposure: The extended connection time gives more opportunity to analyze behavior patterns and identify abusive senders.
The Challenges of Tarpitting
While effective, tarpitting comes with its own set of challenges:
- Resource consumption: Prolonged connections consume server resources that could otherwise be used for legitimate traffic.
- Legitimate bulk mailers: Some legitimate high-volume senders might be adversely affected if tarpitting parameters aren’t carefully tuned.
- Configuration complexity: Finding the right balance between security and performance requires expertise and ongoing adjustment.
- Adaptive spammers: Sophisticated spammers may develop strategies to detect and work around tarpitting measures.
Best Practices for Implementing SMTP Tarpitting
To effectively implement tarpitting without compromising your email infrastructure:
- Graduated approach: Apply increasing delays based on sender reputation and behavior.
- Whitelist trusted senders: Ensure known legitimate senders bypass tarpitting.
- Combined defense: Use tarpitting alongside other protections like SPF, DKIM, and DMARC.
- Monitoring: Continuously analyze traffic patterns to adjust tarpitting parameters.
- Adaptive thresholds: Set different delay thresholds based on time of day, server load, and threat levels.
Anti-Tarpit Tools: Ensuring Email Deliverability
While tarpitting helps protect receiving servers, senders need tools to navigate these protections effectively. This is where anti-tarpit solutions become invaluable for legitimate bulk email senders.
Our unmatched validation service at Gamalogic offers comprehensive anti-tarpit tools with customizable features so you can select the right plan for your own needs. We understand that different businesses have different email volume requirements and deliverability concerns.
We provide three quality levels to choose from:
- Standard-Quality profile: Allows you five seconds of anti-tarpit time, suitable for most business email needs
- High-Quality profile: Exceeds industry standards, giving you up to 50 seconds of anti-tarpit time, ideal for larger marketing campaigns
- Extreme-Quality: Lets you choose anywhere from one second to five minutes of anti-tarpit time, perfect for enterprise-level email operations
These tools work by intelligently managing connection timing, adapting to server responses, and optimizing delivery patterns to ensure your legitimate emails aren’t caught in tarpitting measures.
The Future of SMTP Security
As email threats evolve, so too will protection mechanisms like tarpitting. We’re seeing increasingly sophisticated approaches that combine tarpitting with machine learning algorithms to better distinguish between legitimate and abusive sending patterns.
The future likely holds more adaptive, context-aware tarpitting systems that can make real-time decisions based on complex patterns rather than simple thresholds.
Conclusion
SMTP tarpitting represents an elegant solution to email abuse—using attackers’ need for speed against them. By understanding and respecting these mechanisms, legitimate email senders can better navigate the complex world of email deliverability.
For businesses that depend on reliable email delivery, investing in proper email validation and anti-tarpit solutions isn’t just about avoiding blocks—it’s about being a good citizen of the email ecosystem and ensuring the continued viability of email as a communication channel.
At Gamalogic, we’re committed to helping you maintain that balance with our industry-leading email validation services and adaptable anti-tarpit tools designed to meet your specific needs.
Need help navigating the complexities of email validation and deliverability? Contact our team at Gamalogic today to learn more about our solutions.
You might also like

Email Validation for Deliverability & Email Deliverability Best Practices
Learn how email validation improves deliverability, inbox placement, and sender reputation. Discover SPF, DKIM, DMARC, bounce control, and best practices.

How Spam Bots and Fake Users Can Damage Email Deliverability (And How to Stop Them)
Spam bots and fake users can wreck your email deliverability, harming your sender reputation and reducing inbox placement. Learn how to identify, block, and prevent these threats to protect your list quality and keep your campaigns performing at their best.
How to Use Verified Email Data to Power Engagement Automation
If your automation sequences are built on unverified emails, you aren't just wasting budget; you’re actively damaging your sender reputation. This guide breaks down how to integrate verified email data via Gamalogic to eliminate bounces, bypass spam filters, and ensure your automation workflows reach real inboxes every single time.





 No credit card required
No credit card required

Post your Comment.